Hello guys, In the world of web application security, JSON Web Tokens (JWTs) have gained significant popularity. JWTs provide a secure and efficient way to handle authentication and authorization in modern web applications. In this article, we'll explore the ins and outs of using JWT in a Spring Boot and Spring Security project. From generating tokens to verifying and handling them, we'll cover everything you need to know to leverage JWT effectively in your applications.
What is a JWT (JSON Web Token)?
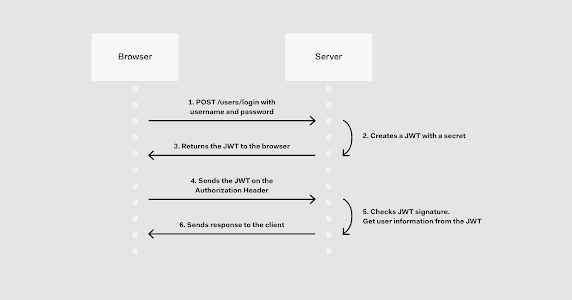
Before diving into implementation details, let's start by understanding what JWTs are. JWTs are compact, URL-safe tokens that consist of three parts: a header, a payload, and a signature. The header contains information about the token's type and the signing algorithm, while the payload carries the actual claims and data.
The signature ensures the integrity and authenticity of the token. JWTs are self-contained, allowing servers to validate and extract information without additional database lookups.
JWTs are stateless, meaning that all the information needed to verify a token is contained within the token itself. This makes them a useful method for authenticating and authorizing users in web applications.
How To Use The JSON Web Token (JWT) In Spring Boot And Spring Security Project
Now that we understand what JWTs are, let's look at how to use them in a Spring Boot and Spring Security project.
To begin, let's set up a Spring Boot project and configure the necessary dependencies. We'll need Spring Security, which provides robust authentication and authorization features, along with libraries like jjwt for working with JWTs. We'll guide you through the process of adding these dependencies and configuring the project.
The first step in using JWTs is generating them upon successful authentication. We'll explore how to configure Spring Security to issue JWTs upon user login. We'll cover concepts like authentication providers, user details services, and token generation. We'll also discuss best practices for including relevant user information and claims in the JWT payload.
Once we have our JWTs, we'll learn how to secure our API endpoints using Spring Security. We'll configure the necessary filters and interceptors to validate incoming JWTs, ensuring that only authenticated and authorized requests are allowed to access protected resources. We'll cover aspects such as token validation, expiration, and handling of unauthorized requests.
JWTs are not only about authentication; they also provide a means for implementing fine-grained authorization. We'll explore how to define roles, permissions, and scopes within JWTs to control access to different parts of your application. We'll demonstrate how to extract and interpret the claims within the token to make informed authorization decisions.
In long-lived applications, it's crucial to handle token expiration and provide mechanisms for refreshing or revoking tokens. We'll discuss strategies for implementing token refresh functionality, enabling users to obtain new JWTs without re-authenticating. We'll also cover approaches for handling token revocation, allowing administrators to invalidate compromised or expired tokens.
To ensure the utmost security of your JWT-based authentication system, we'll provide a set of best practices and highlight potential pitfalls to avoid. We'll cover topics such as token storage, secure token transmission, secure cookie usage, and protection against common vulnerabilities like Cross-Site Scripting (XSS) and Cross-Site Request Forgery (CSRF).
Set an appropriate expiration time for JWTs to balance security and usability. Shorter expiration times minimize the window of opportunity for attackers, while longer expiration times reduce the frequency of token refresh requests. Consider implementing short-lived access tokens and longer-lived refresh tokens for improved security
Ensure that JWTs are transmitted securely over HTTPS to prevent eavesdropping and tampering. Avoid sending tokens over unencrypted channels, such as plain HTTP, as it can expose sensitive information and lead to token theft.
Choose a secure approach for storing JWTs on the client side. Consider using HTTP-only cookies to store tokens, as they are less vulnerable to cross-site scripting attacks. Alternatively, implement token storage in client-side technologies like local storage or session storage, but exercise caution to protect against cross-site scripting vulnerabilities.
Implement mechanisms for token revocation when a user logs out or if a token is compromised. Maintain a blacklist or revoked token store to validate incoming tokens. Additionally, consider using token invalidation techniques like token versioning or token rotation for enhanced security.
Ensure that cryptographic keys used for signing and verifying JWTs are securely managed. Store keys in a secure location and follow industry best practices for key rotation and protection. Consider using asymmetric key pairs for added security, where the private key remains on the server while the public key is used for verification.
When extracting and processing data from JWTs, perform thorough input validation to prevent security vulnerabilities like injection attacks or malicious input exploitation. Sanitize and validate user-supplied input to mitigate risks associated with insecure deserialization or unexpected input manipulation.
Stay updated with the latest security patches and updates for libraries, frameworks, and dependencies used in your Spring Boot and Spring Security project. Promptly address any security vulnerabilities or weaknesses that may arise.
Conclusion
In this article, we have learned how to use JWT for authentication and authorization in a Spring Boot and Spring Security project. We have gone into detail about the JWT structure and how to create and verify tokens. We have also seen how to configure Spring Security to use JWT for authentication and authorization by creating a custom filter and adding it to the Spring Security configuration.
Using JWT in a Spring Boot and Spring Security project provides a secure and scalable solution for authentication and authorization. JWT is lightweight, easy to use, and widely adopted, making it a popular choice for modern web applications.
By following the steps outlined in this article, you can easily implement JWT in your Spring Boot and Spring Security project and ensure secure authentication and authorization for your users.













No comments :
Post a Comment